Many people are still confused with the two important terms. Many who thought that the authentication and authorization are the same, but they are very different.
One goal of security is to ensure that the resource can only be accessed by people who have the right and the right people can access the resource without a hitch.
Imagine in a common plane, there are two classes of passengers, the VIP class and economy class. Security procedures and processes to ensure that passengers occupy seats according to their rights. For that passengers must show proof of a ticket in his name listed there. Then from the passenger list of flight attendants will know that you are entitled to sit in the VIP or economic class. If you hold a ticket to try to sit in economy class flight attendant then VIP will reject you. Especially if you are not holding a ticket, tried to catch the plane, you will definitely kicked.
Authentication: Proof That You are Who You Claim to Be
Before you can provide services to users, service providers need to know who you are. If you declare that you are Tukul Arwana, then prove that you are Tukul. The process of proving who you are (identity) is called authentication. If authentication is successful, it will be a trust relationship is established between service providers and service users.
One proof of identity acceptable to the confidential information. The logic is that if anyone can name a secret that other people might not know unless Tukul, then I will believe that the person is really Tukul.
Another proof of identity acceptable is something unique, just owned by one person in the world. The logic is that if there are people who carry the goods may be owned only Tukul, then I would believe that he is really Tukul. In Chinese kung-fu movies are official delegates of Emperor will bring the royal seal. This stamp is the authentication method is very powerful. Anyone who holds a seal that automatically guaranteed its identity as a messenger of the emperor.
Authentication method based on the confidentiality of information are:
* Password / PIN: Only the owner who knows the password / pin.
* Digital Certificate: Based on asymmetric cryptography which contain confidential information that is private key.
* Private Key: Only the owner knows the private key, others only know the public key.
While authentication methods based on the uniqueness is:
* Retina: There can be no 2 people the same retina pattern.
* Fingerprint: There can be no 2 people the same fingerprints.
* Passport: Only the owner can show photos in passports in accordance with his face.
* Signature: Only the owner can write a perfect signature.
Having established trust relationship, then what services can be enjoyed depending on the user authorization process.
Authorization: What are You Allowed to Do
Authorization is the process of determining what are the services that can be enjoyed by users who have been clearly identified (authenticated user). So before any authorization, should be through a process of authentication. Identity that has been proven on the basis of the authentication process to determine which services a user has the right to enjoy.
The logic is that without knowing who you are, I do not know what can and can not be for you. So without authentication, authorization no. For example when I know you are Tukul Arwana, so I know you can lead the program four eyes, and should not be guided in the Dorce Show. Normally users are not too authentication (anonymous guest) can still enjoy the service, but with very limited access.
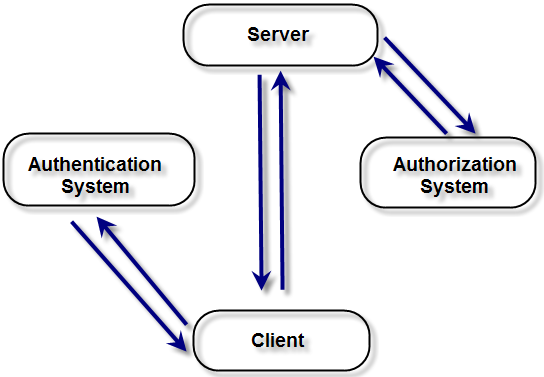
The relationship between client, server, authentication and authorization system can be seen in the picture above. Client before the server can enjoy the service should be through a process of authentication. After successful authentication will be established a trust relationship between client and server so that once a client authentication until logout / exit. For every service request, the server will contact the authorization system to determine whether the client is entitled to the requested service.
Sunday, January 17, 2010
Subscribe to:
Posts (Atom)